
Every day, medical device manufacturers throughout the world race to develop new, highly sophisticated and increasingly connected products. These products offer a wide range of benefits: improved treatments, more precise diagnostics, better patient monitoring, automated control and central reporting, and monitoring of data. However, with increased functionality and connectivity, comes increased risk – dangers notable enough that the FDA in the U.S. has issued cybersecurity guidelines to help OEMs ensure medical devices are safe from cyberattacks.
Even though medical device manufacturers are heavily investing in the development of new medical device technologies, they often lack the security expertise and the technical resources to ensure that high levels of security are built into these solutions. The result, not surprisingly, is the continued manufacturing of devices that are easily compromised by hackers.
FDA cybersecurity guidelines
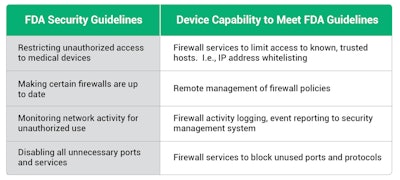
A few of the capabilities recommended in the FDA guidelines include:
- Restricting unauthorized access to medical devices
- Making certain that firewalls are up to date.
- Monitoring network activity for unauthorized use
- Disabling all unnecessary ports and services
To meet these requirements, medical device manufacturers must implement multiple layers of protection, including secure boot, secure firmware updates, firewalls, authentication, security protocols, and intrusion detection/intrusion prevention within the medical device itself.

Medical device security challenges
Medical devices comprise a wildly diverse range of device type and differ greatly from standard PCs or other consumer devices. They are fixed-function devices specifically designed to perform a specialized task. Many of them use a specialized operating system such as VxWorks, FreeRTOS or INTEGRITY, or a stripped-down version of Linux. In most cases, these devices are optimized to minimize processing cycles and memory usage and do not have the extra processing resources required to support traditional security mechanisms.
As a result, standard PC security solutions won’t solve the challenges of embedded devices. In fact, given the specialized nature of embedded systems, Windows-based PC security solutions won’t even run on most embedded devices.
Challenges for medical device security include:
- Critical functionality: Medical devices control life-enabling systems and manage sensitive data.
- Replication: Once designed and built, medical devices are mass produced resulting in thousands to millions of identical devices. Once discovered by a bad actor, a successful attack against one of these devices can be replicated across all the devices.
- Security assumptions: Many medical device engineers have long assumed that their products are not targets for hackers and have not considered security a critical priority.
- Not easily patched: Most medical devices are not easily upgraded, making it difficult to patch security vulnerabilities.
- Long lifecycle: The lifecycle for medical devices may be as long as 10, 15, or even 20, years. Building a device that will stand up to the ever evolving and increasing security requirements of the next two decades is a tremendous challenge.
- Outside the perimeter: Medical devices may be deployed outside of the enterprise security perimeter.
- Unmanageable by users: There is no way for the end user to easily monitor, change, or update an embedded device’s security health.
Security requirements for medical devices
A security solution for medical devices must protect firmware from tampering, secure the data stored by the device, secure communication, and protect the device from cyberattacks. This can only be achieved by building in security from the earliest stages of design.
Unfortunately, there is no single one-size-fits-all security solution for medical devices. Engineers must take into consideration the cost of a security failure (economic, environmental, social, etc.), the risk of attack, available attack vectors, and the cost of implementing a security solution.
Features that need to be considered are:
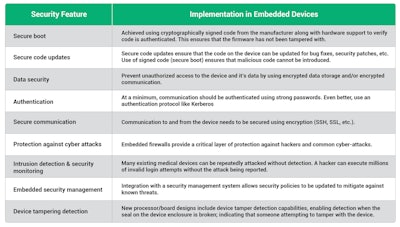
Integrating security into the device
Building protection into the device itself provides a critical security layer that ensures devices are no longer depending on the corporate firewall as their sole layer of security and allows security to be customized to the needs of the device.
The engineering team must be as focused on security as they are on the new capabilities of the device. Building these capabilities into a medical device will enable the device to meet the FDA security guidelines.
Summary
Many of today’s modern medical devices are complex connected computing devices that perform critical functions. Including the latest security protocols and technologies in these devices is an essential design task. Security features must be considered at the very beginning of the design process to ensure the device is protected from the numerous advanced cyber threats they will face in the real world.
Alan Grau has 30 years of experience in telecommunications and the embedded software marketplace. Alan joined Sectigo, a leading Certificate Authority and provider of purpose-built PKI management solutions, in May 2019 as part of the company’s acquisition of Icon Labs, where he was CTO and co-founder, as well as the architect of Icon Labs' award-winning Floodgate Firewall. He is a frequent industry speaker and blogger and holds multiple patents related to telecommunication and security. More info about cybersecurity and protecting the cloud can be found at https://www.sectigo.com.























